Network security is a very essential aspect of todays organizational success in this competitive digital age. Businesses rely on strong network security measures to protect their sensitive data, ensure seamless operations and fight the ever growing number of cyber threats.
This blog explains essential network security tools and zero trust network security. Also network security best practices and the emerging framework for strong cybersecurity.
Why Network Security Matters
Every device, server or system connected to a network presents an entry point for cyber threats. A successful attack can lead to data breaches, operational disruption or financial losses. Network security solutions help reduce these risks by safeguarding infrastructure and ensuring secure data transmission.
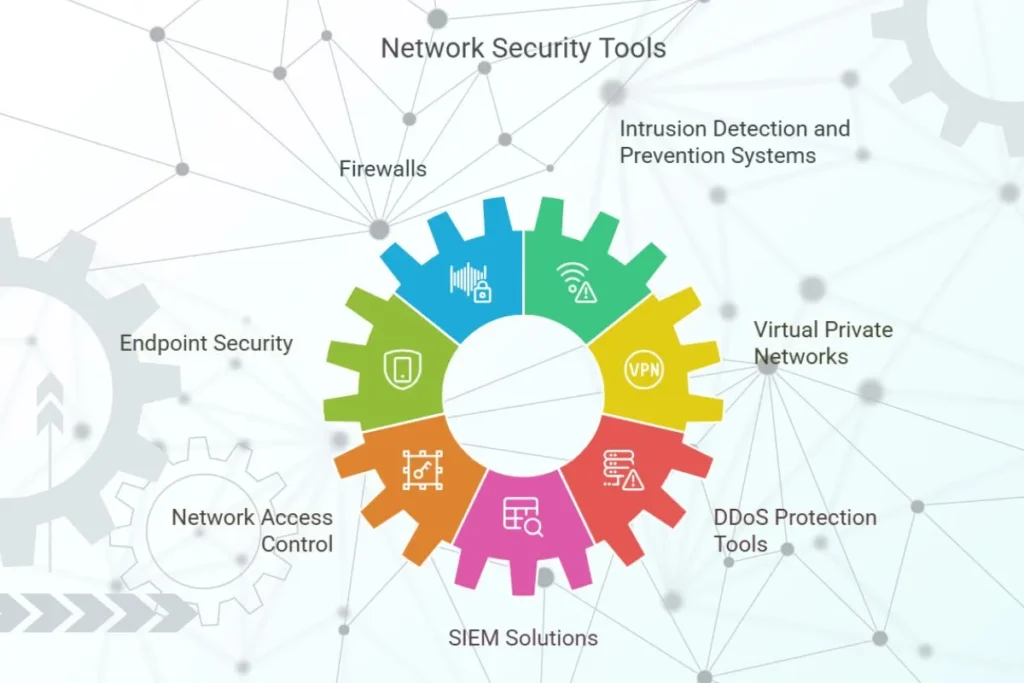
Network Security Tools
A comprehensive network security strategy includes a mix of tools designed to prevent, detect and respond to threats.
1. Firewalls
Firewalls act as gatekeepers for network traffic, blocking unauthorized access while permitting legitimate communications. They are available as hardware, software, or cloud-based solutions.
- Example: A financial institution may use a next generation firewall (NGFW) to analyze traffic in real time, to stop sophisticated attacks.
2. Intrusion Detection and Prevention Systems (IDPS)
IDPS monitor network traffic for unusual activity and either alert administrators (IDS) or actively block threats (IPS).
- Example: A retail company can deploy IDPS to prevent credit card data from being stolen during a transaction.
3. Endpoint Security
Endpoint security solutions protect devices like laptops, smartphones and servers connected to the network. These tools often include antivirus, anti-malware and device management features.
4. Virtual Private Networks (VPNs)
VPNs create encrypted tunnels for data transmission, ensuring secure remote access for employees.
- Example: Remote workers at a global marketing agency can use a VPN to securely access proprietary tools and data.
5. Network Access Control (NAC)
NAC enforces security policies on devices attempting to access the network. Unauthorized devices are denied entry or restricted to specific zones.
6. DDoS Protection Tools
Distributed Denial of Service (DDoS) protection tools reduces cyber attacks designed to overwhelm network resources.
7. SIEM Solutions
Security Information and Event Management (SIEM) systems collect and analyze log data from across the network to detect threats and provide actionable information.
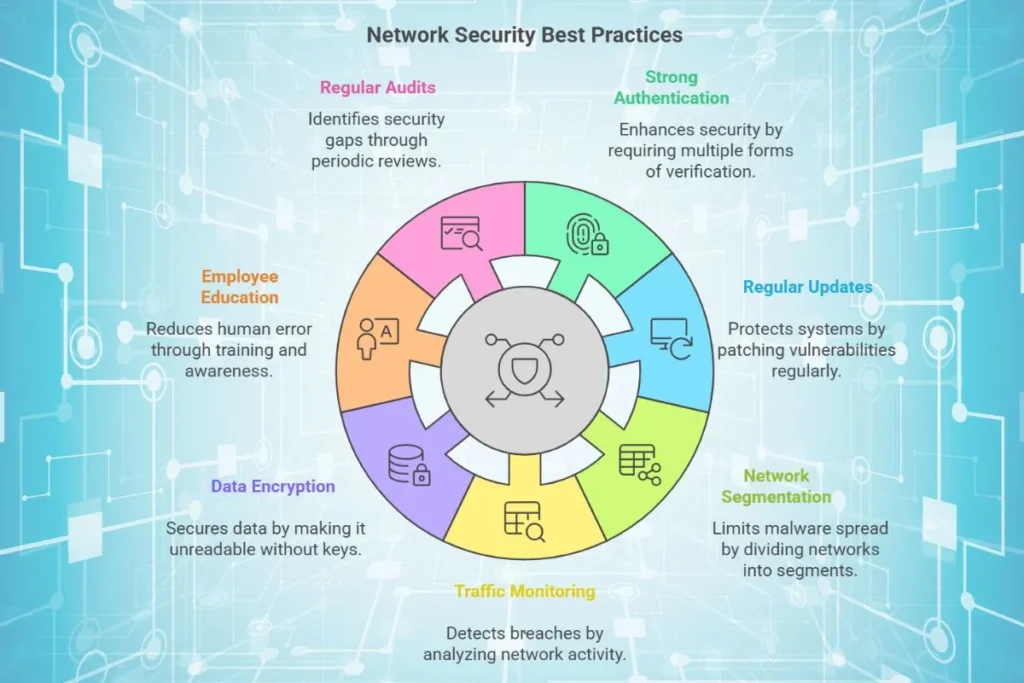
Network Security Best Practices
Following are the proven best practices to ensure long term network security.
1. Enforce Strong Authentication
Use Multi-Factor Authentication (MFA) to add an extra layer of security. Passwords alone are not enough to protect sensitive systems.
2. Regular Software Updates
Update operating systems, applications and network devices regularly to patch vulnerabilities.
- Example: An unpatched router at a manufacturing facility could allow attackers to infiltrate the network.
3. Segment Networks
Divide networks into smaller segments to limit the spread of malware or unauthorized access.
4. Monitor Network Traffic
Use tools like SIEM and IDPS to keep an eye on network activity. Suspicious patterns can indicate attempted breaches.
5. Implement Data Encryption
Encrypt data at rest and in transit to ensure that sensitive information cannot be intercepted.
6. Educate Employees
Human error is a leading cause of breaches. Train employees to recognize phishing attempts, use secure practices and report suspicious activities.
7. Conduct Regular Audits
Periodically review network security configurations and practices to identify gaps and improve defenses.
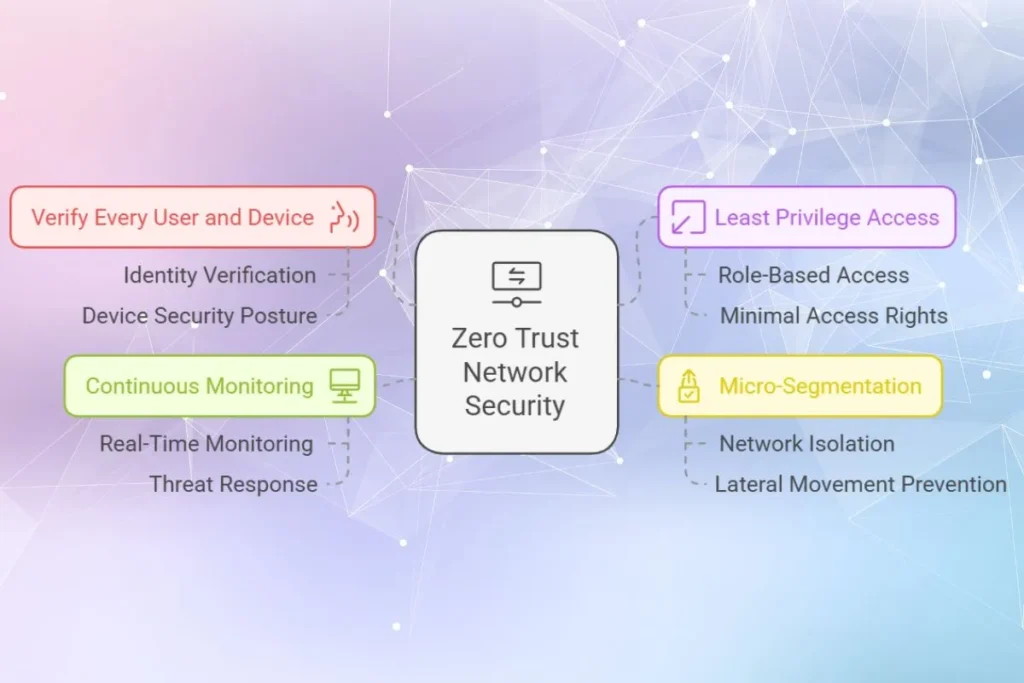
What is Zero Trust Network Security
The Zero Trust model challenges the traditional “trust but verify” approach. Instead, it operates on the principle of “never trust, always verify.”
Key Principles of Zero Trust
- Verify Every User and Device
Access is granted only after verifying the identity and security posture of users and devices. - Least Privilege Access
Users are given the minimum level of access required for their role. - Micro-Segmentation
Network segments are isolated, restricting attackers’ ability to move laterally across the network. - Continuous Monitoring
Activity is continuously monitored to detect and respond to threats in real-time.
Real-World Applications
- A healthcare organization can use Zero Trust to protect patient data, granting access to sensitive records only to authorized staff and devices.
- A tech company implementing Zero Trust can protect intellectual property by strictly controlling developer access to source code repositories.
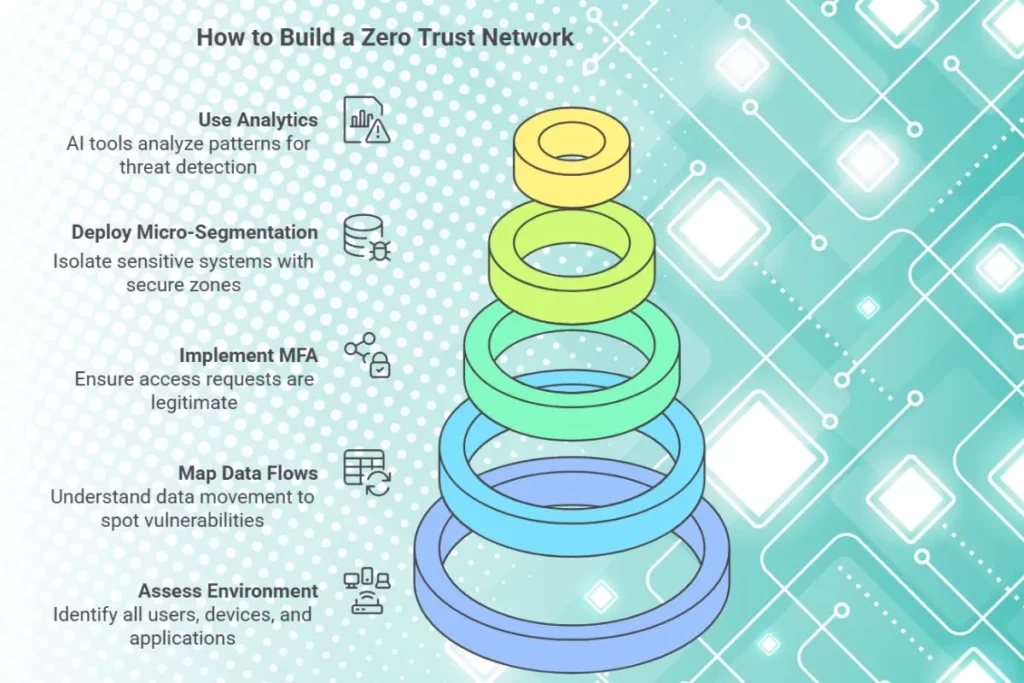
How to Build a Zero Trust Network
1. Assess the Current Environment
Identify all users, devices and applications within the network.
2. Map Data Flows
Understand how data moves across the network to identify vulnerabilities.
3. Adopt Multi Factor Authentication and Identity Management
Implement MFA and identity solutions to ensure that access requests are legitimate.
4. Deploy Micro-Segmentation
Divide the network into secure zones to isolate sensitive systems.
5. Use Analytics for Threat Detection
AI powered tools can analyze patterns and identify potential threats before they go out of control.
Combining Tools, Best Practices and Zero Trust
A strong network security strategy combines modern tools, proven best practices and the Zero Trust model. Enterprises can integrate firewalls, IDPS and SIEM solutions with principles like least privilege access and continuous monitoring to create an airtight defense.
For example, a financial firm using IDPS for traffic monitoring and micro segmentation for data isolation can significantly reduce the risk of breaches. Similarly, a retail chain adopting Zero Trust can ensure secure vendor access to its supply chain systems without compromising overall security.
Conclusion
Network security is a continuous process that requires a mix of advanced tools, adherence to best practices and modern frameworks like Zero Trust. By investing in solutions like firewalls, IDPS and NAC, enterprises can protect sensitive data and maintain operational integrity.
Adopting Zero Trust principles ensures that no entity (internal or external) is trusted without verification. This offers a proactive approach to cybersecurity. Enterprises that prioritize network security, safeguard their assets and also build trust with customers and stakeholders in this increasingly interconnected world.

