As security needs to be more strict in corporate, government and even personal environment, traditional access methods like passwords and ID cards are becoming more vulnerable. Here comes biometrics – a strong technology that uses unique biological characteristics to authenticate users, by adding a layer of security that is personalized and difficult to compromise.
In this article, we shall explore the usage of biometrics in access control systems, how does biometric authentication work? Also, we shall learn the different types of biometric access control systems for businesses, their advantages and challenges of incorporating them.
Why Use Biometrics in Access Control System
Biometric technology is all about identity verification. By analyzing a person’s unique physical or behavioral attributes, biometric systems provide access only to authorized individuals, which makes unauthorized entry significantly harder. Unlike PIN codes or access cards that can be lost or shared, biometric attributes are inherently individual, which are impossible to lose or forget.
This unique approach to security makes biometric systems specially useful in environments where high security is essential, such as government facilities, corporate offices, research labs and healthcare institutions.
How does Biometric Authentication Works
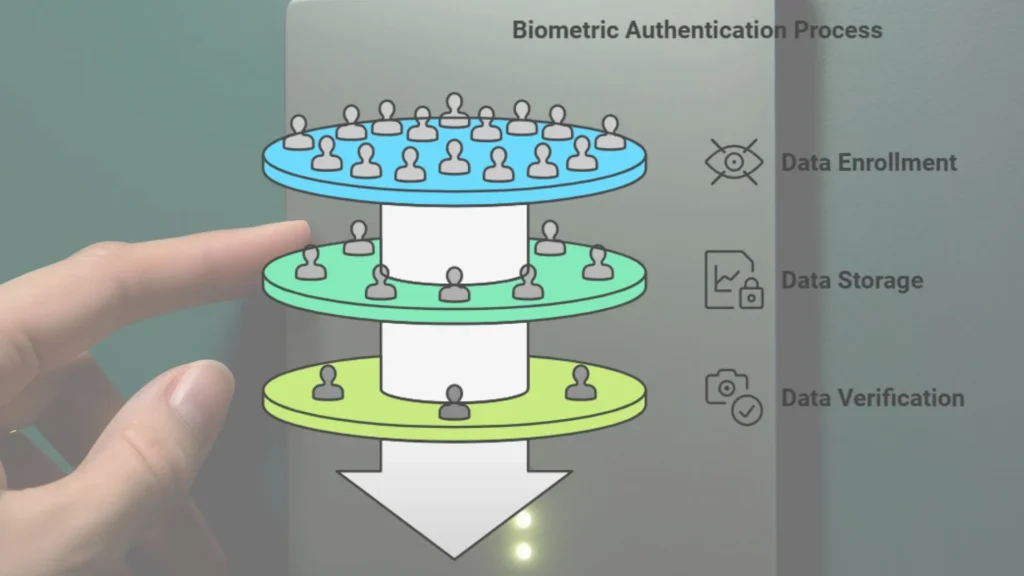
Biometric authentication generally involves three main steps:
1. Enrollment: The system captures and stores the user’s biometric data (e.g., fingerprint or face scan) as a reference.
2. Storage: The captured biometric data is converted into a unique mathematical model and securely stored.
3. Verification: During each access attempt, the system compares the scanned biometric data with the stored data. If it matches, access is granted.
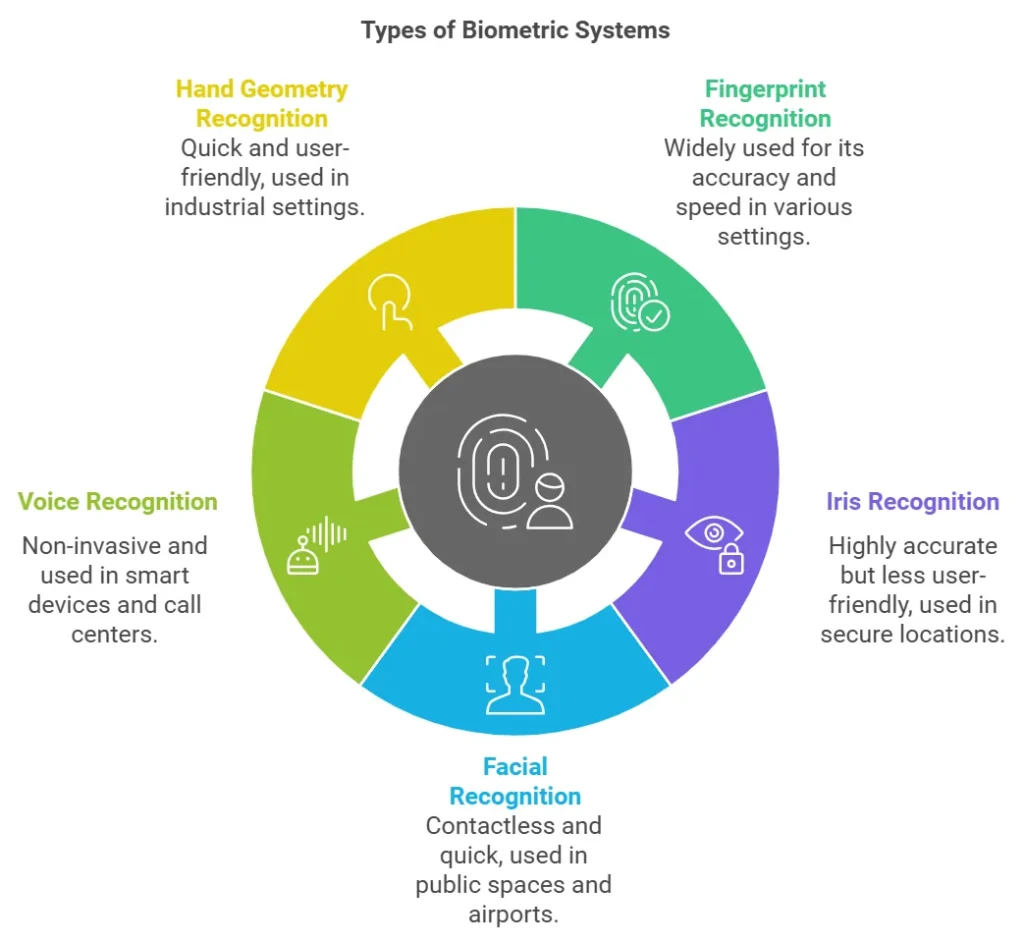
Types of Biometric Systems
Several types of biometrics are commonly used in access control, each with its own method of capturing and analyzing personal data. Here is a look at some of the most widely used types:
1. Fingerprint Recognition
Fingerprint recognition is one of the most widely used biometric technologies, thanks to its accuracy, speed and ease of implementation.
– How It Works: Users place their finger on a sensor, which captures an image of the fingerprint pattern. The system then compares it to a stored image in the database.
– Pros: It is quick, cost effective and user friendly.
– Cons: Can sometimes be bypassed with spoofing techniques and certain conditions (like cuts or wet fingers) can affect recognition.
– Common Uses: Commonly used in smartphones, office buildings and high security areas.
2. Iris Recognition
Iris recognition involves scanning the unique pattern in the colored ring around the pupil.
– How It Works: The system captures an image of the iris and analyzes its pattern. This pattern is then matched with pre stored patterns to verify identity.
– Pros: Highly accurate and nearly impossible to replicate.
– Cons: More expensive to implement and less user friendly due to the need for precise positioning during scanning.
– Common Uses: Common in high security government and corporate buildings, airports and secure data centers.
3. Facial Recognition
Facial recognition uses algorithms to analyze the unique features of an individual’s face.
– How It Works: The system captures facial features such as the distance between the eyes, jawline and shape of the nose. It then matches this data against pre stored data.
– Pros: It is contactless and quick to operate.
– Cons: It can be less accurate with changes in lighting, facial expressions or angles. Concerns also exist around privacy and potential misuse.
– Common Uses: Widely used in airports, public spaces and smartphones.
4. Voice Recognition
Voice recognition technology identifies individuals based on the unique qualities of their voice, including pitch, tone and rhythm.
– How It Works: The user speaks into a microphone and the system analyzes vocal characteristics to match with a voiceprint in the database.
– Pros: It is non invasive and contactless.
– Cons: Background noise, health conditions and aging can impact accuracy.
– Common Uses: Call centers, smart home devices and remote authentication.
5. Hand Geometry Recognition
Hand geometry recognition involves analyzing the shape and size of the hand and fingers.
– How It Works: Users place their hand on a scanner, which captures the dimensions of the hand. The system then compares this data to pre stored handprints.
– Pros: It is quick and user friendly.
– Cons: Less unique than other biometric methods and may not be suitable for individuals with hand injuries.
– Common Uses: Construction sites, manufacturing plants and time keeping systems.
Pros and Cons of Using Biometrics in Access Control
Biometric access control systems bring unique benefits but also come with some short comings. Here is a breakdown in detail:
Pros of Biometric Access Control
1. Enhanced Security: Biometrics make it nearly impossible for unauthorized users to get access, as biometric attributes are unique to each individual.
2. Convenience: Users don’t need to remember passwords or carry cards, which simplifies the login process.
3. High Accuracy: Most biometric systems, especially iris and fingerprint recognition, offer high levels of accuracy and reliability.
4. Reduced Fraud: Biometrics prevent fraud by ensuring that only the authorized individual can access a secure area or system.
5. Non-transferable: Biometric data cannot be shared or replicated, unlike traditional access methods.
6. Time-Saving: Biometric access is faster than entering a password or scanning a card.
7. Audit Trail: Biometric systems can log each entry and exit, providing a detailed audit trail.
Cons of Biometric Access Control
1. Privacy Concerns: Biometric data is sensitive and if compromised, can’t be reset like a password. Concerns exist about how and where biometric data is stored and managed.
2. High Initial Costs: The implementation of biometric systems, particularly those requiring advanced technology like iris scanners, can be costly.
3. Performance Issues: Factors like lighting, health conditions, or physical changes can affect the accuracy of biometric systems.
4. Risk of Spoofing: Despite advancements, certain biometrics, like facial and fingerprint recognition, can still be spoofed by sophisticated methods.
5. User Acceptance: Some individuals may be uncomfortable with certain biometric methods, such as facial or iris recognition.
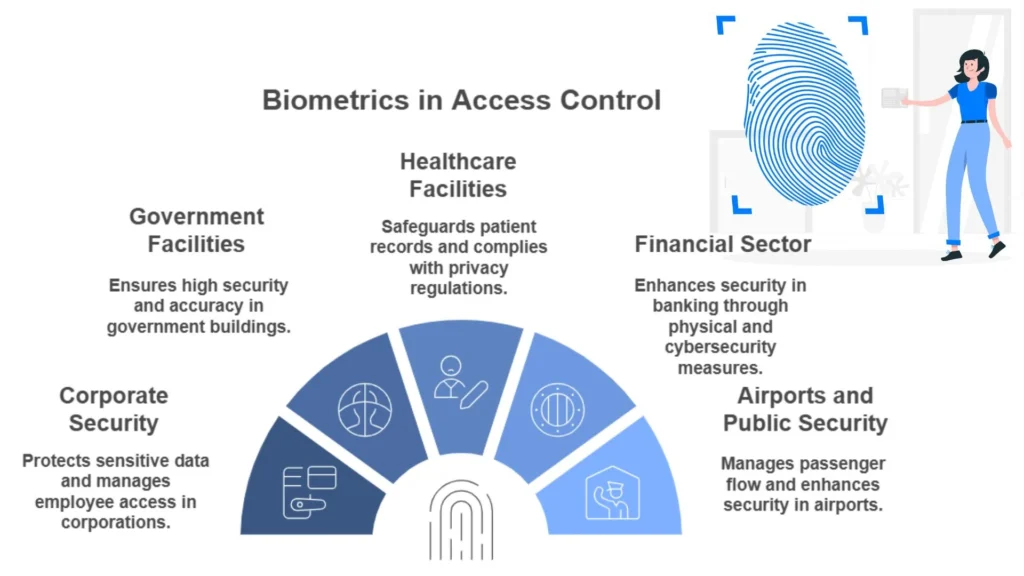
Real World Applications of Biometrics in Access Control
Biometric systems are used in a variety of industries, with some applications becoming almost universal. Here are a few real world examples:
1. Corporate Security
Corporations use biometric systems to protect sensitive data, manage employee access and secure restricted areas. By employing biometrics, businesses can ensure that only authorized employees gain access to specific areas or information, which helps to prevent data leaks and unauthorized entry.
Example: Companies like Google and Microsoft use fingerprint and facial recognition to control access to high security zones within their offices.
2. Government Facilities
Government buildings generally require top level security due to the sensitive nature of the information they handle. Biometric technology is ideal for these settings, which offers high accuracy and security.
Example: The U.S. Department of Homeland Security uses biometric data in airports to screen international travelers through facial recognition, to speed up immigration checks and enhance security.
3. Healthcare Facilities
In healthcare, biometrics is used to control access to patient records, which ensures confidentiality and compliance with regulations such as HIPAA in the U.S. Healthcare facilities also use biometrics to track staff access to sensitive areas like pharmacies and laboratories.
Example: Many hospitals use fingerprint recognition to grant access to patient records, safeguarding personal health information to ensure compliance with privacy regulations.
4. Financial Sector
Financial institutions like banks use biometric systems for both physical security (controlling access to vaults) and cybersecurity (for online banking access). Biometrics can also be integrated into ATMs to replace or supplement traditional PIN systems.
Example: Citibank uses voice recognition for customer identification in call centers, which enhances security and improves customer experience by reducing the need for lengthy verification processes.
5. Airports and Public Security
Airports and public security agencies use biometrics to manage passenger flow, verify identities and enhance overall security.
Example: Dubai International Airport has introduced biometric gates with facial and iris recognition to streamline the immigration process, which reduces waiting times and enhances security.
Key Considerations for Implementing Biometric Access Control Systems
For organizations considering biometric access control, several factors should be taken into account to ensure both security and usability:
1. Data Storage: Biometric data should be stored securely, ideally using encryption and other data protection measures. Cloud storage of biometric data also requires strong safeguards against breaches.
2. User Privacy: Organizations must comply with privacy laws and ensure that biometric data is collected, stored and used responsibly. Transparent policies on data usage can help to relieve privacy concerns.
3. Redundancy Systems: Biometrics should be part of a multi layered security strategy. Implementing backup methods like PIN codes or access cards can prevent access issues if a biometric system fails.
4. Cost vs. Benefit: While biometric systems offer high security, they can be costly. Organizations should weigh the cost of implementation against the benefits, by considering factors like the level of security required and the potential return on investment.
5. Environmental Compatibility: Assess the environment to determine the best biometric method. Fingerprint scanners, for instance, may not work well in dusty or wet conditions, while iris or hand geometry might be more suitable.
6. Fallback Options: Ensure there are alternative access methods for instances where biometric identification fails (e.g., a PIN or access card as backup).
The Future of Biometrics in Access Control
The future of biometrics looks promising, with emerging technologies likely to deal some of the limitations we see today. Trends such as the integration of AI for enhanced accuracy, multimodal biometrics that combine multiple biometric methods and advancements in security protocols are making biometrics even more secure and efficient.
Emerging Technologies in Biometrics
1. AI Enhanced Biometrics: Artificial intelligence is improving the accuracy and speed of biometric recognition, which makes the systems smarter and more adaptable to real world scenarios.
2. Multimodal Biometrics: Using multiple biometrics, such as combining facial recognition with fingerprint or iris scans, enhances accuracy and reduces the risk of spoofing.
3. Behavioral Biometrics: These involve analyzing user behavior, like typing speed or mouse movements, which provides an additional layer of security that is harder to imitate.
Conclusion
Biometrics offer a powerful, personalized approach to access control, to enhance security across a wide range of industries. From fingerprint recognition in corporate offices to iris scanning in government facilities, biometrics provide convenience and strong security. However, organizations must check privacy concerns and costs and implementation before incorporating biometric systems.
As advancements in AI and multimodal recognition continue, biometrics are set to become even more reliable and widely adopted, which makes it a strong, scalable and future proof access control solution.

