Day by day the frauds and digital threats are increasing, hence cybersecurity has become one of the most important aspects of protecting sensitive information and assets. Traditional security methods, while effective, still struggle to keep up with increasingly sophisticated cyberattacks. This is where machine learning (ML) comes into picture. ML enables real time fraud detection, threat analysis and response to security threats on an unprecedented scale.
This post will explain the role of machine learning in cybersecurity, how machine learning enhances cybersecurity, how it identifies anomalies, prevents fraud and fights various threats, with real world examples to illustrate these applications.
What is the Role of Machine Learning in Cybersecurity?
Machine learning in cybersecurity refers to using algorithms that can learn from data patterns and improve over time. Unlike static rule based systems, ML models adapt to new data, which makes them more effective at detecting unknown and evolving threats. These models are trained on large datasets that contain normal and malicious activities, allowing them to recognize unusual behaviors and respond automatically.
Some benefits of ML in cybersecurity include:
– Real time threat detection
– Improved accuracy in detecting anomalies
– Ability to adapt to new types of attacks
– Enhanced predictive analysis and threat prevention
1. Threat Detection: Identifying Attacks in Real Time
Detecting cyber threats as they happen is important to prevent extensive damage. ML models analyze large amounts of network traffic and device behavior to identify suspicious patterns that could indicate an attack.
For instance, ML can identify:
– Phishing emails by analyzing patterns in sender behavior, content and links
– Malware through classification of files, based on known malware features and signatures
– Intrusion attempts by recognizing patterns of access that deviate from normal user behavior
Real World Example: IBM Watson for Cyber Security
IBM Watson, an AI platform, uses machine learning to detect threats by analyzing millions of cybersecurity documents and reports to provide security analysts with actionable insights. The platform is capable of understanding natural language, which makes it easier to recognize new threats in real time.
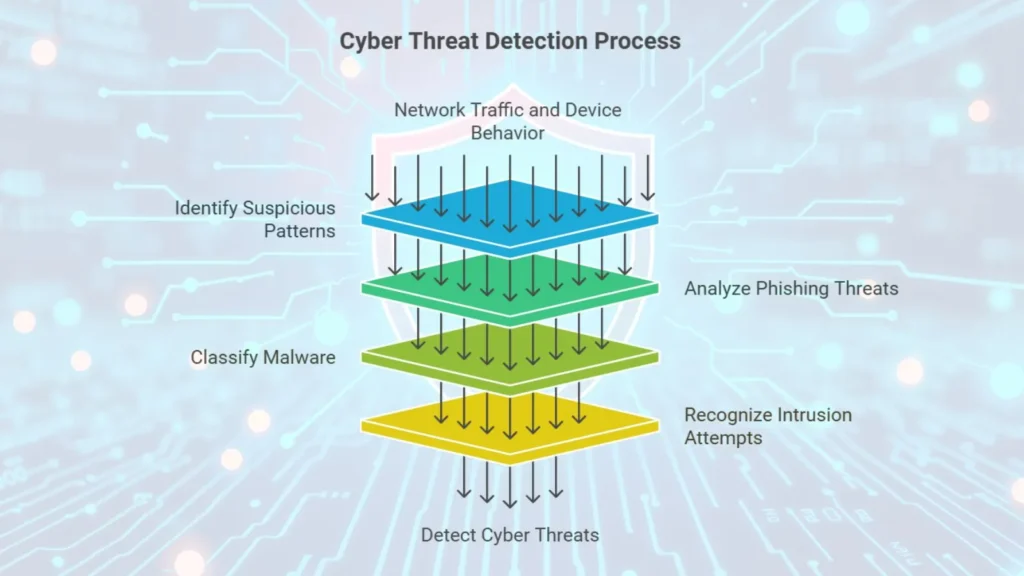
2. Anomaly Detection: Spotting Unusual Patterns
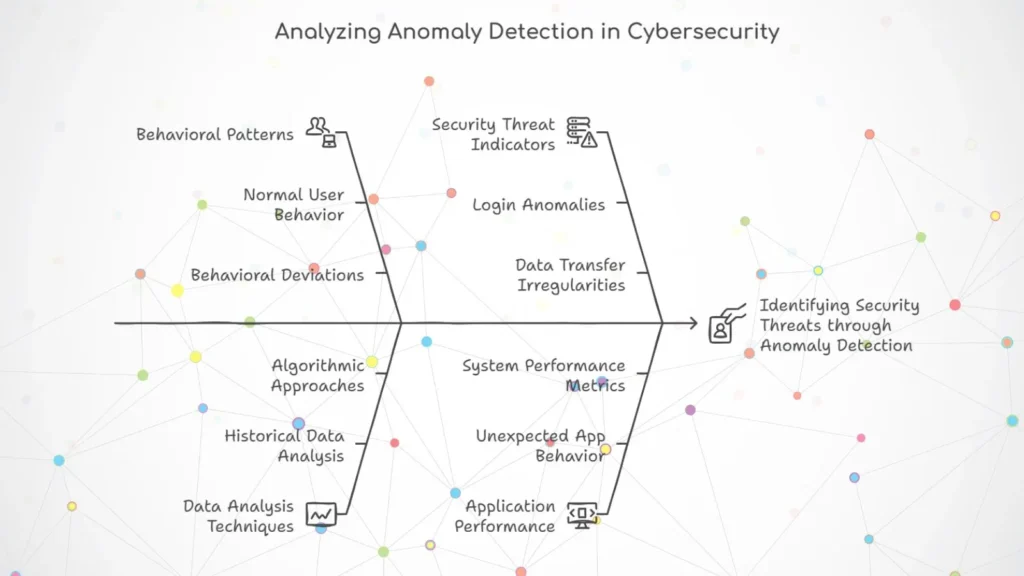
Anomaly detection is one of the most powerful ML applications in cybersecurity. It works by learning normal behavior patterns and pin-pointing deviations that may indicate a potential security threat.
ML algorithms, such as clustering and neural networks, help to identify anomalies by analyzing historical data. Common applications include:
– Identifying unusual login attempts
– Spotting irregular data transfer volumes
– Detecting unexpected application behavior
Example: CrowdStrike’s Falcon Platform
CrowdStrike’s Falcon platform uses ML to analyze endpoint behavior, to detect anomalies such as unusual file executions or abnormal processes. This allows the platform to pin-point and respond to potential attacks even when specific malware signatures are not present.
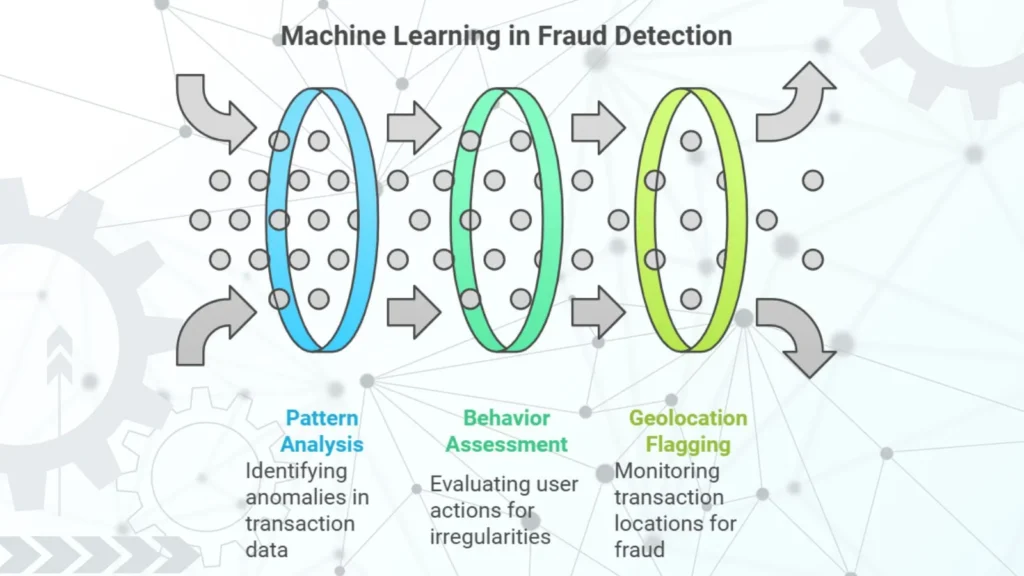
3. Fraud Prevention: Safeguarding Financial Transactions
Fraud detection is a high stakes application of ML in cybersecurity, particularly in financial services. Traditional fraud detection relies on predefined rules that can miss sophisticated, evolving fraud tactics. Machine learning adds a dynamic layer, which allows systems to detect fraud in real time by analyzing patterns across various transaction data points.
Applications in fraud prevention:
– Analyzing credit card transactions for unusual patterns
– Identifying fraudulent account activity by assessing login and purchase behavior
– Flagging suspicious online purchases based on geolocation
Real World Example: PayPal’s ML Based Fraud Detection
PayPal uses machine learning to examine millions of transactions per day, which identifies and blocks fraudulent activities before they cause damage. The ML models analyze transaction metadata, such as the time, location and amount, to detect anomalies indicative of fraud.
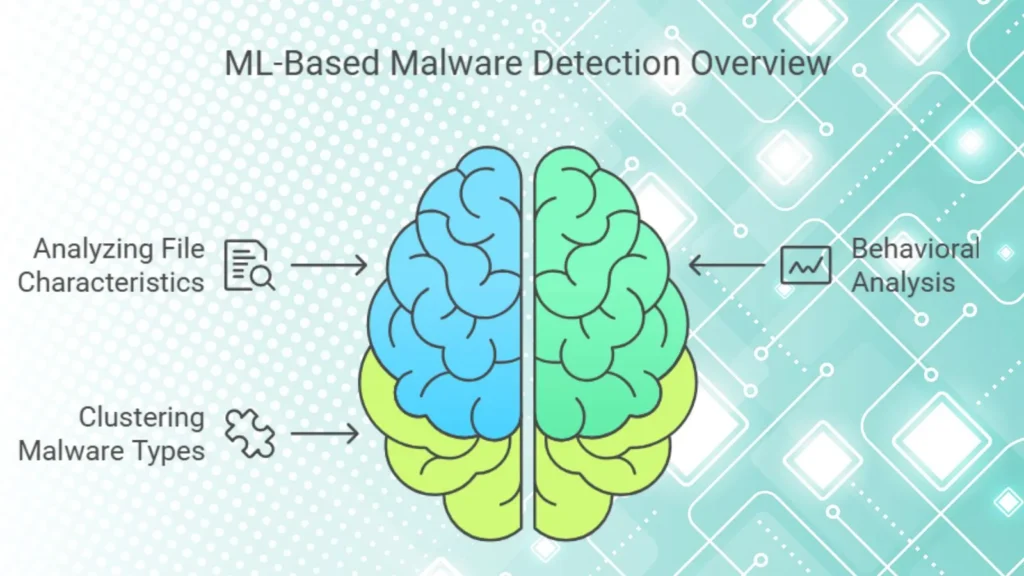
4. Malware Detection and Classification
Malware detection identifies malicious software designed to harm or penetrate systems. Traditional signature based detection methods have limited capacity because they require an updated database of known malware. In contrast, ML based malware detection learns from patterns and behavior rather than known signatures, which makes it more effective against everyday attacks.
ML can classify malware by:
– Analyzing file characteristics
– Using behavioral analysis to detect unusual execution patterns
– Clustering malware types based on similarities
Real World Example: Cylance’s AI Powered Antivirus
Cylance uses machine learning to detect and prevent malware attacks. Its models classify files as benign or malicious based on a deep analysis of their code, which enables the software to block new and unknown malware types before they can execute.
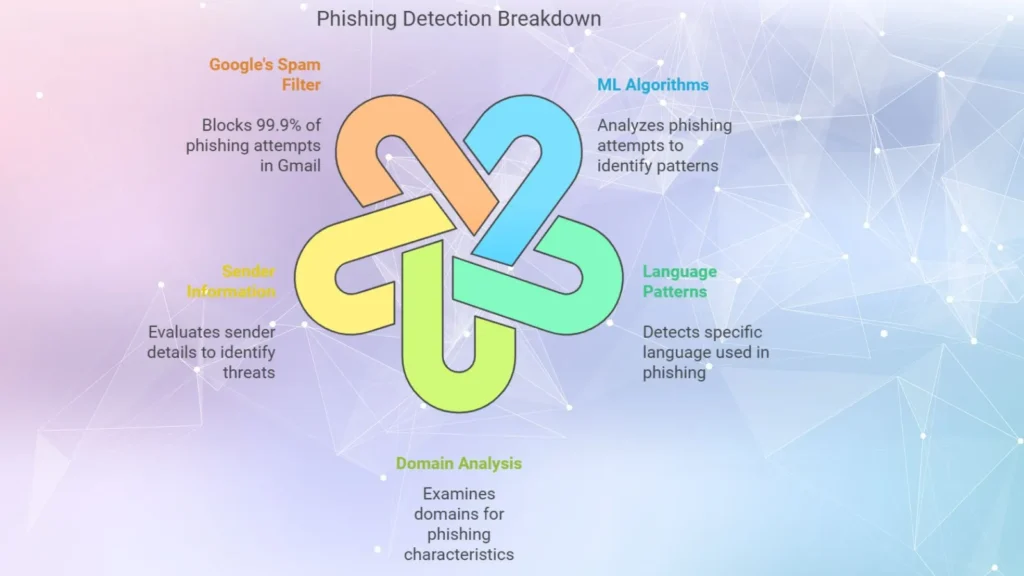
5. Phishing Detection
– ML algorithms can analyze thousands of phishing attempts and learn to identify characteristics of phishing emails, such as specific language patterns, domains and sender information.
– Google’s machine learning powered spam filter blocks over 99.9% of phishing attempts in Gmail, which reduces the likelihood of users falling prey to malicious links and data breaches.
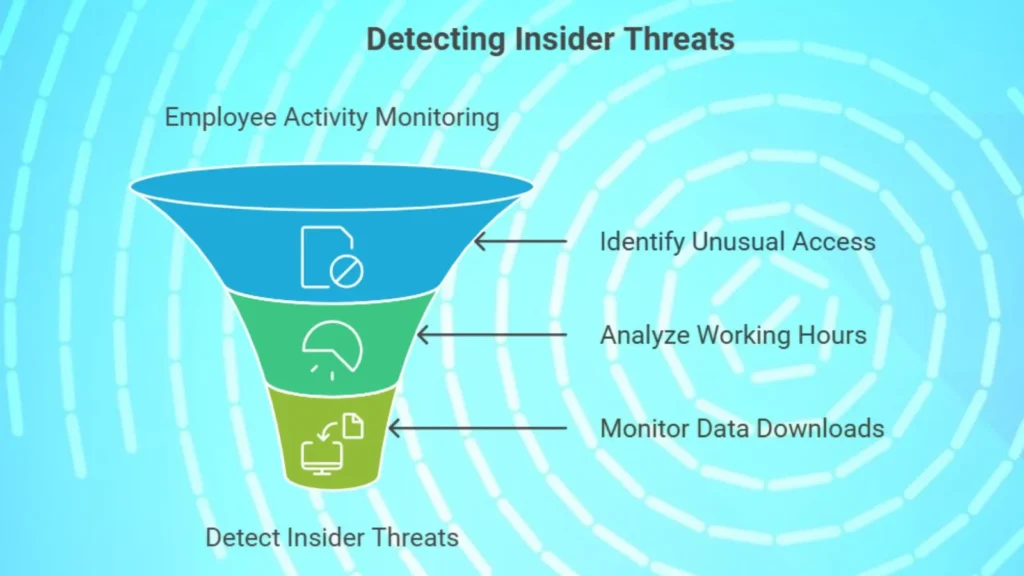
6. Identifying Insider Threats: Monitoring Employee Behavior
Insider threats means the cyber threats originating from within an organization, are among the hardest to detect. Machine learning algorithms can monitor employee activity and detect unusual behaviors, such as unauthorized access to sensitive files or attempts to transfer or remove data, by comparing with normal behavioral patterns.
Common indicators of insider threats:
– Sudden access to high level files by low level employees
– Unusual working hours or accessing the network remotely without precedent
– Large data downloads to personal devices
Example: Splunk’s User Behavior Analytics
Splunk’s User Behavior Analytics (UBA) applies ML algorithms to identify risky behaviors and insider threats. UBA models analyze patterns in employee activity, such as login times, frequency of file access and data transfer, to flag any potential insider threats.
ML Based Cybersecurity Solutions
There are several ML based cybersecurity platforms that companies can adopt to safeguard their systems:
1. Darktrace:
– Darktrace’s cybersecurity solution uses ML based anomaly detection to identify threats in real time, monitoring network traffic to detect irregularities and prevent potential breaches.
– Darktrace’s “Enterprise Immune System” operates similarly to a human immune system, detecting and responding to emerging threats by learning “normal” network behaviors.
2. Cisco Umbrella:
– Cisco Umbrella uses machine learning to provide a secure internet gateway, predicting potential threats by monitoring domain names, IPs and URLs in real-time.
– Cisco’s ML algorithms detect patterns associated with phishing and malware sites, blocking users from accessing them.
3. IBM Watson for Cybersecurity:
– IBM Watson integrates machine learning to process large volumes of cybersecurity research data, allowing organizations to predict and defend against sophisticated threats.
– With its advanced natural language processing (NLP) capabilities, IBM Watson can analyze unstructured data like research papers and blogs to stay updated on the latest cybersecurity trends and emerging threats.
4. Microsoft Defender Advanced Threat Protection:
Uses Machine Learning to monitor cloud infrastructure, endpoints and email for unusual activity.
5. FireEye:
Uses ML powered threat intelligence to identify and respond to advanced cyberattacks.
6. Sophos Intercept X:
Employs deep learning models to detect malware and ransomware, focusing on predictive protection.
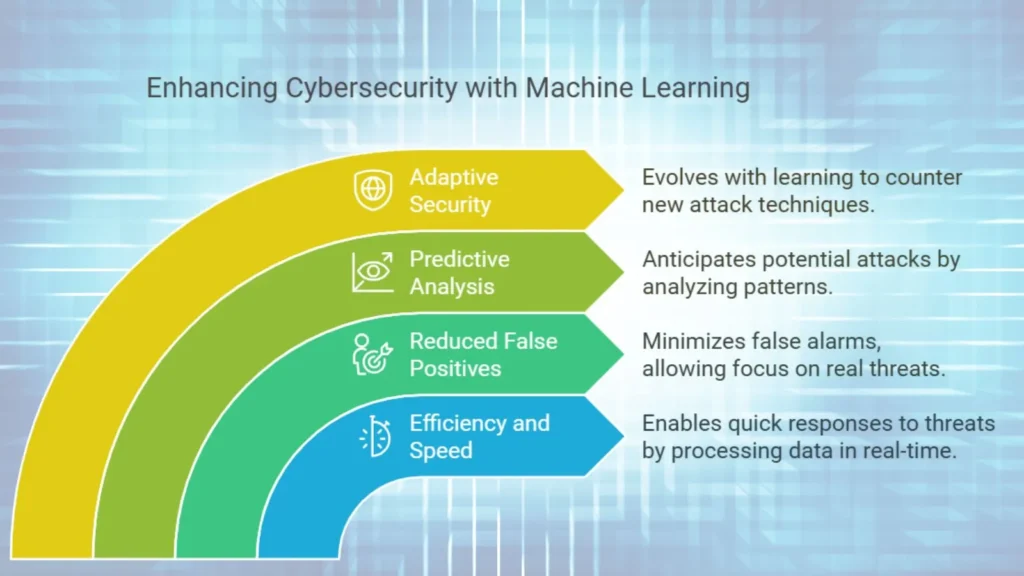
Benefits of Machine Learning in Cybersecurity
1. Efficiency and Speed:
ML models can process large amounts of data in real time, which enables quick responses to threats.
2. Reduced False Positives:
By continuously learning, ML algorithms can reduce false alarms, which enables cybersecurity teams to focus on real threats.
3. Predictive Analysis:
ML can anticipate potential attacks by analyzing patterns, which helps to prevent security incidents before they occur.
4. Adaptive Security:
Unlike rule based systems, ML models evolve and improve as they learn, to keep up with the latest attack techniques.
Challenges and Limitations of Machine Learning in Cybersecurity
While machine learning offers substantial advantages, it has to face following challenges:
1. Data Quality and Quantity
– ML models require large volumes of high quality data to accurately identify threats. Inconsistent or incomplete data can lead to inaccurate predictions, which affects the effectiveness of the model.
2. Adversarial Attacks
– Adversarial attacks, where cybercriminals manipulate input data to mislead ML models, pose a significant threat. Attackers can introduce malicious data to deceive the model into ignoring a threat, creating new security risks.
3. Privacy Concerns
– Handling sensitive data for machine learning requires strict data privacy measures. Many companies must address regulatory requirements and ensure they handle data ethically, which can be challenging in a rapidly evolving field.
4. Complexity of Implementation
– Integrating machine learning into cybersecurity requires skilled professionals and significant resources, which is difficult for smaller organizations. Additionally, ML models need constant updates and maintenance to remain effective.
5. High Costs:
Developing and maintaining ML based cybersecurity solutions can be costly for smaller organizations.
The Future of Machine Learning in Cybersecurity
As cyber threats grow more sophisticated, machine learning is becoming more important in cybersecurity strategies. Key future trends include:
1. Increased Use of Deep Learning:
Deep learning models will enhance threat detection by analyzing more complex data.
2. AI Driven Cybersecurity Operations Centers (CSOCs):
AI powered CSOCs will allow companies to monitor threats continuously with minimal human intervention. This helps analysts to detect, manage and resolve incidents faster, to stay ahead of cybercriminals.
3. Automation in Threat Response:
Self learning models will detect threats and autonomously respond to attacks, which minimizes response times.
4. Enhanced Behavioral Analytics:
By using ML, cybersecurity solutions will gain more precise behavioral analytics, which improves threat detection and makes it easier to distinguish between legitimate user activities and malicious behavior.
Conclusion
Machine learning is transforming cybersecurity, by helping organizations with tools to proactively detect, prevent and respond to cyber threats. From real time anomaly detection to fraud prevention and insider threat monitoring, ML models provide the flexibility, speed and adaptability required to stay ahead of evolving cyber risks.
As ML based solutions advance, they will continue to reshape how we think about cybersecurity and by offering more comprehensive and intelligent defenses against modern threats. By understanding and embracing these technologies, businesses can build strong cybersecurity strategies that are prepared for both current and future challenges.
With the right ML based approach, organizations can achieve a level of cybersecurity that protects their assets and strengthens trust with customers, to ensure a safer digital environment for everyone.

